Threat actors can abuse Microsoft 365 Direct Send to send unauthenticated emails that appear to originate from internal users. Because Direct Send does not require credentials, MFA, or a sign-in event, it bypasses identity-based protections and enables high-trust phishing and internal impersonation attacks.
In many tenants, this is a configuration risk that exists by default and often goes unnoticed. Microsoft’s research shows this technique being used with lures such as “password expiration” messages that masquerade as legitimate Microsoft communications.
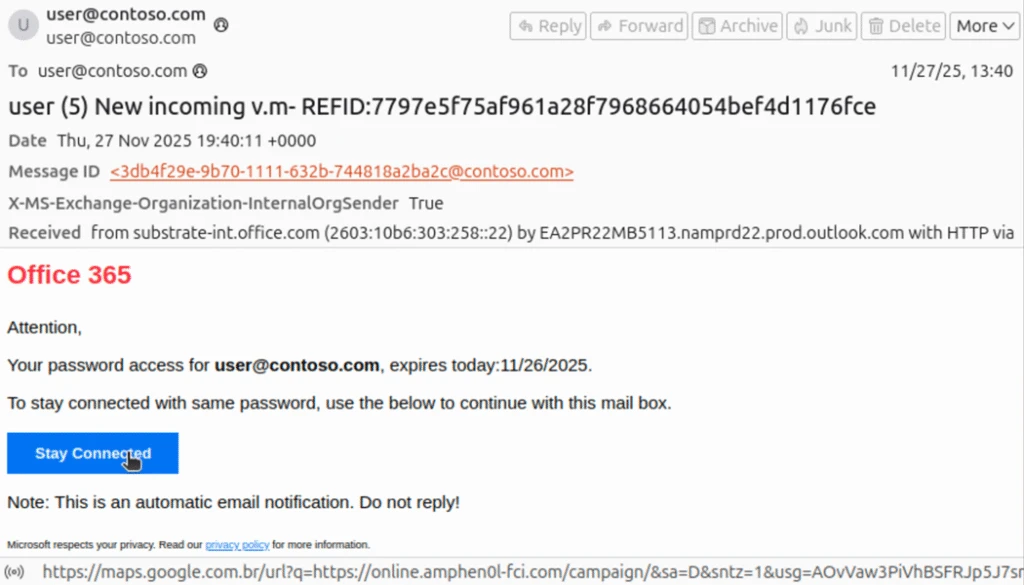
Direct Send is intended for legacy devices such as printers, scanners, and applications that need to send email without SMTP authentication. However, when left enabled or loosely restricted, it can be exploited to deliver spoofed internal messages that evade Conditional Access, MFA, and identity logging entirely.
Overe actively detects and enforces protection against Direct Send abuse by identifying exposure and applying policy-based remediation where Direct Send is not explicitly required.

Overe continuously assesses Microsoft 365 tenants for Direct Send exposure and enforces secure configuration through guided, policy-driven controls — helping organisations eliminate this risk without disrupting legitimate business workflows.