Token Protection Conditional Access now in Overe
Attackers don’t always breach your environment by breaking MFA or guessing passwords. Increasingly, they take a shortcut: stealing an active session token and bypassing most of your defenses entirely.
In Microsoft 365, these tokens—Primary Refresh Tokens (PRTs)—are issued when users authenticate and allow them to access services without reentering credentials. If a token is stolen, it can often be reused from a different device without triggering your Conditional Access rules.
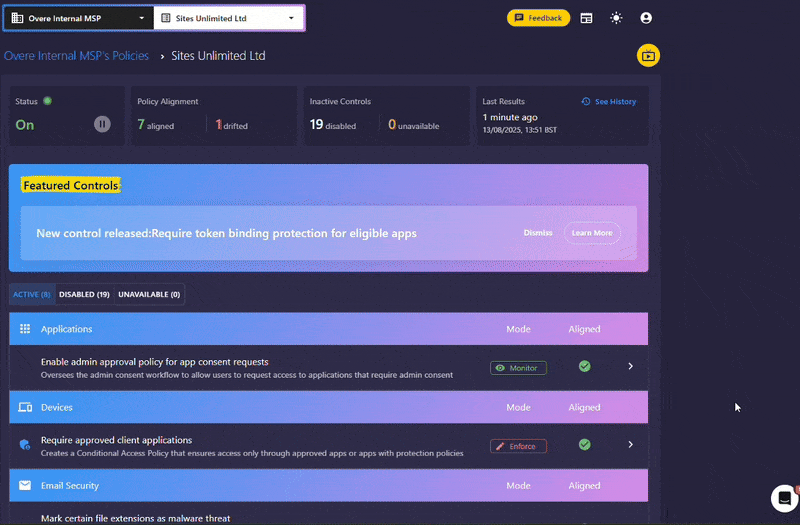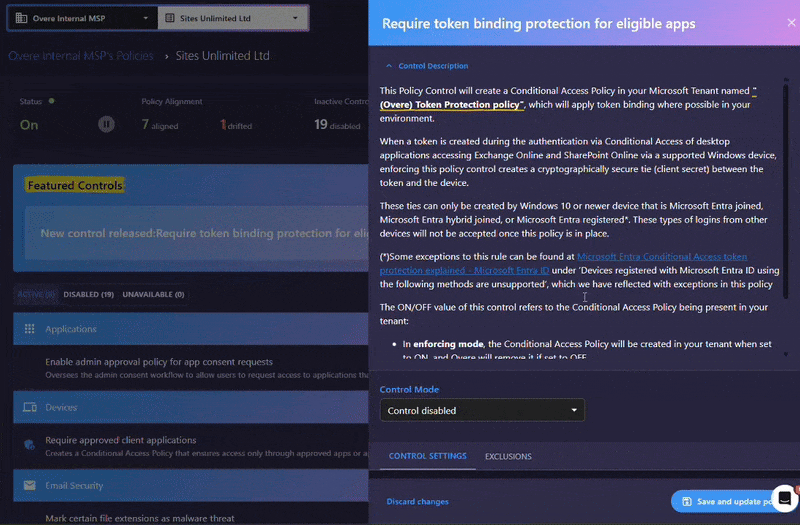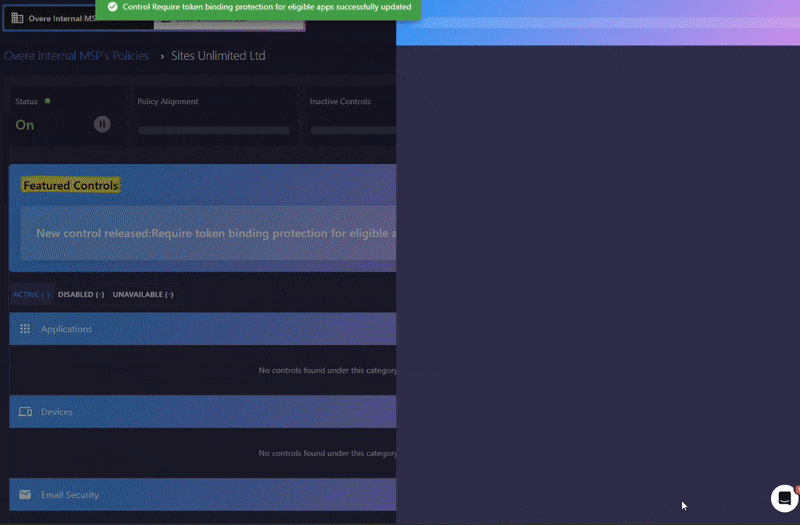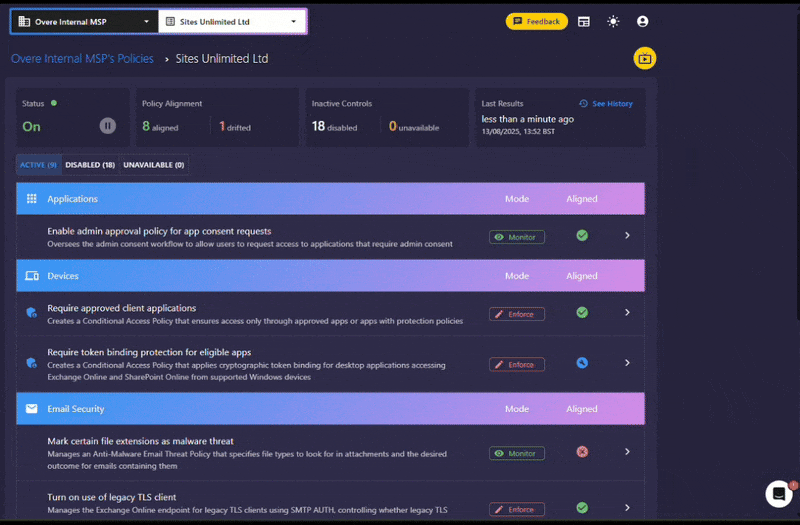
Microsoft’s Token Protection policy changes this dynamic. When enabled, PRTs are cryptographically bound to the device they were issued to. If the token is copied to another device, it becomes invalid. This prevents attackers from using stolen tokens for lateral movement or persistent access.
Licensing requirement: Token Protection is available with a Microsoft Entra ID P1 license. This is already included in Microsoft 365 Business Premium and Microsoft 365 E3, as well as the standalone Entra ID P1 license, so most organisations can enable it at no extra cost.
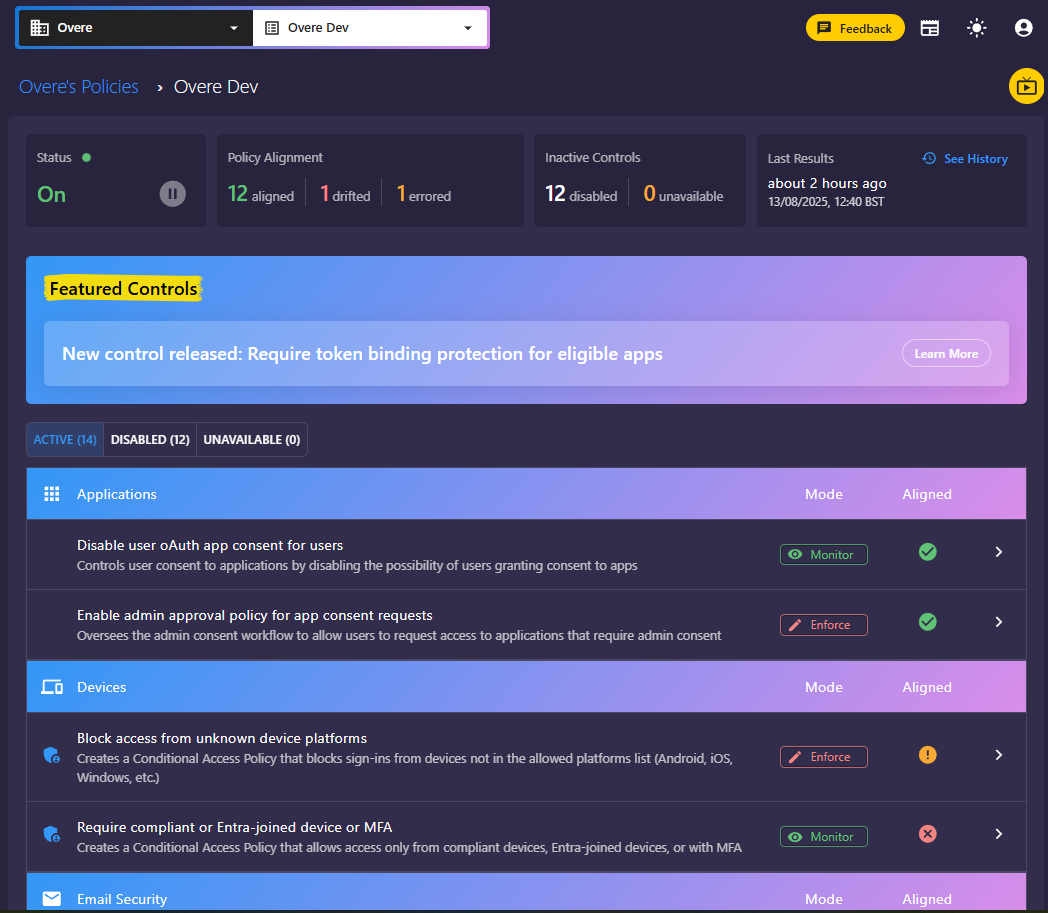
Why We’re Adding It to Overe
Keeping up with new Microsoft security features is a moving target.Overe’s role is making sure you don’t miss changes that matter to your environment. Token Protection is now part of Overe’s Conditional Access policy set.
By integrating it into Overe:
How Token Protection Works

Learn more about Token Protection in Microsoft’s documentation
Start with Overe